Chronologie aller Bände (1 - 104)

Die Reihenfolge beginnt mit dem Buch "Agent Based Modelling of Urban Systems". Wer alle Bücher der Reihe nach lesen möchte, sollte mit diesem Band von Mohammad-Reza Namazi-Rad beginnen. Der zweite Teil der Reihe "Pattern Recognition" ist am 23.02.2020 erschienen. Mit insgesamt 104 Bänden wurde die Reihe über einen Zeitraum von ungefähr 10 Jahren fortgesetzt. Der neueste Band trägt den Titel "Consolidated Ada 2022 Reference Manual. Volume 1 - Core Language".
- Anzahl der Bewertungen für die gesamte Reihe: 10
- Ø Bewertung der Reihe: 4.6
- Start der Reihe: 11.01.2017
- Neueste Folge: 04.06.2027
Diese Reihenfolge enthält 81 unterschiedliche Autoren.
- Autor: Namazi-Rad, Mohammad-Reza
- Anzahl Bewertungen: 0
- Ø Bewertung:
- Medium: Buch
- Veröffentlicht: 11.01.2017
- Genre: Sonstiges
Agent Based Modelling of Urban Systems
This book constitutes revised, selected, and invited papers from the First International Workshop on Agent Based Modelling of Urban Systems, ABMUS 2016, held in conjunction with AAMAS 2016 in Singapore in May 2016.
The 11 papers presented in this volume were carefully reviewed and selected from 20 submissions. They were organized in topical sections named: urban systems modeling; traffic simulation in urban modeling; and applications.
- Autor: Koch, Fernando
- Anzahl Bewertungen: 0
- Ø Bewertung:
- Medium: E-Book
- Veröffentlicht: 20.02.2019
- Genre: Sonstiges
Artificial Intelligence in Health
The 18 revised full papers included in this volume were carefully selected from the 26 papers accepted for presentation out of 42 initial submissions. The papers present AI technologies with medical applications and are organized in three tracks: agents in healthcare; data science and decision systems in medicine; and knowledge management in healthcare.
- Autor: Palaiahnakote, Shivakumara
- Anzahl Bewertungen: 0
- Ø Bewertung:
- Medium: Buch
- Veröffentlicht: 23.02.2020
- Genre: Sonstiges
Pattern Recognition
This two-volume set constitutes the proceedings of the 5th Asian Conference on ACPR 2019, held in Auckland, New Zealand, in November 2019.
The 9 full papers presented in this volume were carefully reviewed and selected from 14 submissions. They cover topics such as: classification; action and video and motion; object detection and anomaly detection; segmentation, grouping and shape; face and body and biometrics; adversarial learning and networks; computational photography; learning theory and optimization; applications, medical and robotics; computer vision and robot vision; pattern recognition and machine learning; multi-media and signal processing and interaction.
- Autor: Palaiahnakote, Shivakumara
- Anzahl Bewertungen: 0
- Ø Bewertung:
- Medium: Buch
- Veröffentlicht: 23.02.2020
- Genre: Sonstiges
Pattern Recognition
This two-volume set constitutes the proceedings of the 5th Asian Conference on ACPR 2019, held in Auckland, New Zealand, in November 2019.
The 9 full papers presented in this volume were carefully reviewed and selected from 14 submissions. They cover topics such as: classification; action and video and motion; object detection and anomaly detection; segmentation, grouping and shape; face and body and biometrics; adversarial learning and networks; computational photography; learning theory and optimization; applications, medical and robotics; computer vision and robot vision; pattern recognition and machine learning; multi-media and signal processing; and interaction.
- Autor: Bernhard, Matthew
- Anzahl Bewertungen: 0
- Ø Bewertung:
- Medium: Buch
- Veröffentlicht: 07.08.2020
- Genre: Sonstiges
Financial Cryptography and Data Security
The papers feature four Workshops: The 1st Asian Workshop on Usable Security, AsiaUSEC 2020, the 1st Workshop on Coordination of Decentralized Finance, CoDeFi 2020, the 5th Workshop on Advances in Secure Electronic Voting, VOTING 2020, and the 4th Workshop on Trusted Smart Contracts, WTSC 2020.
The AsiaUSEC Workshop contributes an increase of the scientific quality of research in human factors in security and privacy. In terms of improving efficacy of secure systems, the research included an extension of graphical password authentication. Further a comparative study of SpotBugs, SonarQube, Cryptoguard and CogniCrypt identified strengths in each and refined the need for improvements in security testing tools.
The CoDeFi Workshop discuss multi-disciplinary issues regarding technologies and operations of decentralized finance based on permissionless blockchain. The workshop consists of two parts; presentations by all stakeholders, and unconference style discussions.
The VOTING Workshop cover topics like new methods for risk-limited audits, new ethods to increase the efficiency of mixnets, verification of security of voting schemes election auditing, voting system efficiency, voting system usability, and new technical designs for cryptographic protocols for voting systems, and new way of preventing voteselling by de-incentivising this via smart contracts.
The WTSC Workshop focuses on smart contracts, i.e., self-enforcing agreements in the form of executable programs, and other decentralized applications that are deployed to and run on top of specialized blockchains.
- Autor: De Marsico, Maria
- Anzahl Bewertungen: 0
- Ø Bewertung:
- Medium: Buch
- Veröffentlicht: 23.12.2020
- Genre: Sonstiges
Pattern Recognition Applications and Methods
This book contains revised and extended versions of selected papers from the 9th International Conference on Pattern Recognition, ICPRAM 2020, held in Valletta, Malta, in February 2020. The 7 full papers presented were carefully reviewed and selected from 102 initial submissions.
The papers describe applications of pattern recognition techniques to real-world problems, interdisciplinary research, experimental and theoretical studies yielding new insights that advance pattern recognition methods are especially encouraged.
- Autor: Hotho, Andreas
- Anzahl Bewertungen: 0
- Ø Bewertung:
- Medium: Buch
- Veröffentlicht: 30.09.2021
- Genre: Sonstiges
The Semantic Web – ISWC 2021
The papers included in this volume deal with the latest advances in fundamental research, innovative technology, and applications of the Semantic Web, linked data, knowledge graphs, and knowledge processing on the Web. Papers are organized in a research track, resources and in-use track. The research track details theoretical, analytical and empirical aspects of the Semantic Web and its intersection with other disciplines. The resources track promotes the sharing of resources which support, enable or utilize semantic web research, including datasets, ontologies, software, and benchmarks. And finally, the in-use-track is dedicated to novel and significant research contributions addressing theoretical, analytical and empirical aspects of the Semantic Web and its intersection with other disciplines.
- Autor: Stephanidis, Constantine
- Anzahl Bewertungen: 0
- Ø Bewertung:
- Medium: Buch
- Veröffentlicht: 13.11.2021
- Genre: Sonstiges
HCI International 2021 - Late Breaking Papers: Cognition, Inclusion, Learning, and Culture
A total of 5222 individuals from academia, research institutes, industry, and governmental agencies from 81 countries submitted contributions, and 1276 papers and 241 posters were included in the volumes of the proceedings that were published before the start of the conference. Additionally, 174 papers and 146 posters are included in the volumes of the proceedings published after the conference, as “Late Breaking Work” (papers and posters). The contributions thoroughly cover the entire field of HCI, addressing major advances in knowledge and effective use of computers in a variety of application areas.
- Autor: Batina, Lejla
- Anzahl Bewertungen: 0
- Ø Bewertung:
- Medium: Buch
- Veröffentlicht: 29.01.2022
- Genre: Krimi
Security, Privacy, and Applied Cryptography Engineering
This book constitutes the refereed proceedings of the 11th International Conference on Security, Privacy, and Applied Cryptography Engineering, SPACE 2021, held in Kolkata, India, in December 2021.
The 13 full papers presented were carefully reviewed and selected from 42 submissions. This annual event is devoted to various aspects of security, privacy, applied cryptography, and cryptographic engineering. This is a very challenging field, requiring the expertise from diverse domains, ranging from mathematics to solid-state circuit design.
- Autor: Groth, Paul
- Anzahl Bewertungen: 0
- Ø Bewertung:
- Medium: Buch
- Veröffentlicht: 20.07.2022
- Genre: Sonstiges
The Semantic Web: ESWC 2022 Satellite Events
This book constitutes the proceedings of the satellite events held at the 19th Extended Semantic Web Conference, ESWC 2022, during May—June in Hersonissos, Greece, 2022.
The included satellite events are: the poster and demo session; the PhD symposium; industry track; project networking; workshops and tutorials.
During ESWC 2022, the following ten workshops took place:10th Linked Data in Architecture and Construction Workshop (LDAC 2022); 5th International Workshop on Geospatial Linked Data (GeoLD 2022); 5th Workshop on Semantic Web solutions for large-scale biomedical data analytics (SeMWeBMeDA 2022); 7th Natural Language Interfaces for the Web of Data (NLIWOD+QALD 2022); International Workshop on Knowledge Graph Generation from Text (Text2KG 2022); 3rd International Workshop on Deep Learning meets Ontologies and Natural Language Processing (DeepOntoNLP 2022); 1st Workshop on Modular Knowledge (ModularK 2022); Third International Workshop On Knowledge Graph Construction (KGCW 2022); Third International Workshop On Semantic Digital Twins (SeDIT 2022); and the 1st International Workshop on Semantic Industrial Information Modelling (SemIIM 2022).
- Autor: Wong, Lung-Hsiang
- Anzahl Bewertungen: 0
- Ø Bewertung:
- Medium: Buch
- Veröffentlicht: 27.10.2022
- Genre: Sonstiges
Collaboration Technologies and Social Computing
The 18 full and 4 work-in-process papers presented in this volume were selected from 37 submissions and underwent careful double-blind peer review. The papers focus on innovative technical, human and organizational approaches to expand collaboration support including computer science, management science, design science, cognitive and social science.
- Autor: Reiser, Hans P.
- Anzahl Bewertungen: 0
- Ø Bewertung:
- Medium: Buch
- Veröffentlicht: 02.01.2023
- Genre: Krimi
Secure IT Systems
- Autor: De Marsico, Maria
- Anzahl Bewertungen: 0
- Ø Bewertung:
- Medium: Buch
- Veröffentlicht: 27.01.2023
- Genre: Sonstiges
Pattern Recognition Applications and Methods
This book contains revised and extended versions of selected papers from the 10th and 11th International Conference on Pattern Recognition, ICPRAM 2021 and 2022, held in February 2021 and 2022. Due to COVID-19 pandemic the conferences were held virtually. Both conferences received in total 204 submissions from which 8 full papers were carefully reviewed and selected for presentation in this volume. The papers span a wide range of investigation as well as development lines, which of course always reflect the last trends of research in the pattern recognition community.
- Autor: You, Ilsun
- Anzahl Bewertungen: 0
- Ø Bewertung:
- Medium: Buch
- Veröffentlicht: 14.03.2023
- Genre: Krimi
Information Security Applications
The 25 papers included in this book were carefully reviewed and selected from 76 submissions. They were organized in topical sections as follows: network security; cryptography; vulnerability analysis; privacy enhancing technique; security management; security engineering.
- Autor: Troya, Javier
- Anzahl Bewertungen: 0
- Ø Bewertung:
- Medium: Buch
- Veröffentlicht: 19.03.2023
- Genre: Sonstiges
Service-Oriented Computing – ICSOC 2022 Workshops
Workshop on Adaptive Service-oriented and Cloud Applications (ASOCA 2022), 3rd International Workshop on AI-enabled Process Automation (AI-PA 2022), 3rd International Workshop on Architectures for Future Mobile Computing and Internet of Things (FMCIoT 2022), and 18th International Workshop on Engineering Service-Oriented Applications and Cloud Services (WESOACS 2022) held in conjunction with the 20th International Conference on Service-Oriented Computing, ICSOC 2022. The conference was held in Sevilla, Spain, in November/December 2022.
- Autor: Fang, Fei
- Anzahl Bewertungen: 0
- Ø Bewertung:
- Medium: Buch
- Veröffentlicht: 22.03.2023
- Genre: Krimi
Decision and Game Theory for Security
- Autor: Kavun, Elif Bilge
- Anzahl Bewertungen: 0
- Ø Bewertung:
- Medium: Buch
- Veröffentlicht: 28.03.2023
- Genre: Krimi
Constructive Side-Channel Analysis and Secure Design
The 12 full papers included in this book were carefully reviewed and selected from 28 submissions. They were organized in topical sections as follows: fault-injection analyses and countermeasures; side-channel analyses and countermeasures; attacks on PQC and countermeasure; and analyses and tools.
- Autor: Seo, Seung-Hyun
- Anzahl Bewertungen: 0
- Ø Bewertung:
- Medium: Buch
- Veröffentlicht: 31.03.2023
- Genre: Krimi
Information Security and Cryptology – ICISC 2022
The 24 full papers included in this book were carefully reviewed and selected from 69 submissions. They were organized in topical sections as follows: Public Key Encryption with Hierarchical Authorized Keyword Search, Implicit Key-stretching Security of Encryption Schemes.
- Autor: Jourdan, Guy-Vincent
- Anzahl Bewertungen: 1
- Ø Bewertung: 5.0
- Medium: Buch
- Veröffentlicht: 01.04.2023
- Genre: Krimi
Foundations and Practice of Security
The 26 regular and 3 short papers presented in this book were carefully reviewed and selected from 83 submissions. The papers have been organized in the following topical sections: Cryptography; Machine Learning; Cybercrime and Privacy; Physical-layer Security; Blockchain; IoT and Security Protocols; and Short Papers.
- Autor: Nicosia, Giueseppe
- Anzahl Bewertungen: 0
- Ø Bewertung:
- Medium: Buch
- Veröffentlicht: 07.04.2023
- Genre: Krimi
Machine Learning, Optimization, and Data Science
The total of 84 full papers presented in this two-volume post-conference proceedings set was carefully reviewed and selected from 226 submissions. These research articles were written by leading scientists in the fields of machine learning, artificial intelligence, reinforcement learning, computational optimization, neuroscience, and data science presenting a substantial array of ideas, technologies, algorithms, methods, and applications.
- Autor: Nicosia, Giueseppe
- Anzahl Bewertungen: 0
- Ø Bewertung:
- Medium: Buch
- Veröffentlicht: 18.04.2023
- Genre: Krimi
Machine Learning, Optimization, and Data Science
The total of 84 full papers presented in this two-volume post-conference proceedings set was carefully reviewed and selected from 226 submissions. These research articles were written by leading scientists in the fields of machine learning, artificial intelligence, reinforcement learning, computational optimization, neuroscience, and data science presenting a substantial array of ideas, technologies, algorithms, methods, and applications.
- Autor: Wyrzykowski, Roman
- Anzahl Bewertungen: 0
- Ø Bewertung:
- Medium: Buch
- Veröffentlicht: 27.04.2023
- Genre: Roman
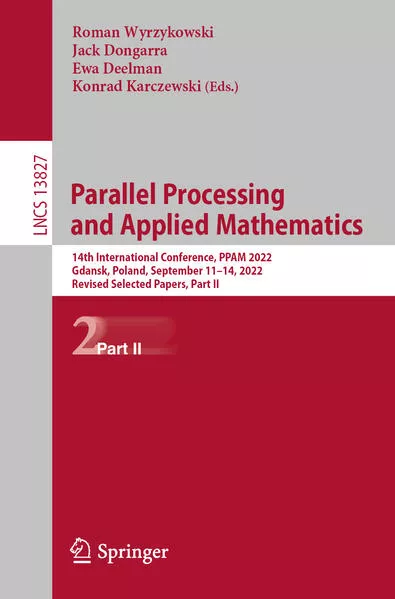
Parallel Processing and Applied Mathematics
This two-volume set, LNCS 13826 and LNCS 13827, constitutes the proceedings of the 14th International Conference on Parallel Processing and Applied Mathematics, PPAM 2022, held in Gdansk, Poland, in September 2022.
The 77 regular papers presented in these volumes were selected from 132 submissions. For regular tracks of the conference, 33 papers were selected from 62 submissions.
The papers were organized in topical sections named as follows:
Part I: numerical algorithms and parallel scientific computing; parallel non-numerical algorithms; GPU computing; performance analysis and prediction in HPC systems; scheduling for parallel computing; environments and frameworks for parallel/cloud computing; applications of parallel and distributed computing; soft computing with applications and special session on parallel EVD/SVD and its application in matrix computations.
Part II: 9th Workshop on Language-Based Parallel Programming (WLPP 2022); 6th Workshop on Models,Algorithms and Methodologies for Hybrid Parallelism in New HPC Systems (MAMHYP 2022); first workshop on quantum computing and communication; First Workshop on Applications of Machine Learning and Artificial Intelligence in High Performance Computing (WAML 2022); 4th workshop on applied high performance numerical algorithms for PDEs; 5th minisymposium on HPC applications in physical sciences; 8th minisymposium on high performance computing interval methods; 7th workshop on complex collective systems.
- Autor: Wyrzykowski, Roman
- Anzahl Bewertungen: 0
- Ø Bewertung:
- Medium: Buch
- Veröffentlicht: 28.04.2023
- Genre: Roman
Parallel Processing and Applied Mathematics
The 77 regular papers presented in these volumes were selected from 132 submissions. For regular tracks of the conference, 33 papers were selected from 62 submissions.
The papers were organized in topical sections named as follows:
Part I: numerical algorithms and parallel scientific computing; parallel non-numerical algorithms; GPU computing; performance analysis and prediction in HPC systems; scheduling for parallel computing; environments and frameworks for parallel/cloud computing; applications of parallel and distributed computing; soft computing with applications and special session on parallel EVD/SVD and its application in matrix computations.
Part II: 9th Workshop on Language-Based Parallel Programming (WLPP 2022); 6th Workshop on Models, Algorithms and Methodologies for Hybrid Parallelism in New HPC Systems (MAMHYP 2022); first workshop on quantum computing and communication; First Workshop on Applications of Machine Learning and Artificial Intelligence in High Performance Computing (WAML 2022); 4th workshop on applied high performance numerical algorithms for PDEs; 5th minisymposium on HPC applications in physical sciences; 8th minisymposium on high performance computing interval methods; 7th workshop on complex collective systems.
- Autor: Hämmerli, Bernhard
- Anzahl Bewertungen: 0
- Ø Bewertung:
- Medium: Buch
- Veröffentlicht: 08.06.2023
- Genre: Krimi
Critical Information Infrastructures Security
The 16 full papers and 4 short papers included in this volume were carefully reviewed and selected from 26 submissions. They are organized in topical sections as follows: protection of cyber-physical systems and industrial control systems (ICS); C(I)IP organization, (strategic) management and legal aspects; human factor, security awareness and crisis management for C(I)IP and critical services; and future, TechWatch and forecast for C(I)IP and critical services.
- Autor: Gruss, Daniel
- Anzahl Bewertungen: 0
- Ø Bewertung:
- Medium: Buch
- Veröffentlicht: 10.06.2023
- Genre: Krimi
Detection of Intrusions and Malware, and Vulnerability Assessment
The 12 full papers and 1 short paper presented in this volume were carefully reviewed and selected from 43 submissions. The papers are organized in thematical sections named: Side Channels Attacks; Security and Machine Learning; Cyber Physical System Security; Security Issues when Dealing with Users; Analysis of Vulnerable Code; Flow Integrity and Security.
- Autor: Warren, David S.
- Anzahl Bewertungen: 0
- Ø Bewertung:
- Medium: Buch
- Veröffentlicht: 17.06.2023
- Genre: Sonstiges
Prolog: The Next 50 Years
After a first chapter that gently introduces the Prolog programming language using examples, the next 7 papers discuss general views of the language, possible extensions for the future, and how Prolog can generally be used to solve problems; the next 5 papers explore ideas and experiences of teaching Prolog programming and then 2 papers discuss technology that has been developed for help in that teaching; the next 3 papers describe new languages based on Prolog which show future directions for logic programming; the next 5 chapters explain the applications that were the finalists for the 2022 Alain Colmerauer Prize; and the final 8 papers describe applications developed using the Prolog language, demonstrating the language’s range.
- Autor: Atluri, Vijayalakshmi
- Anzahl Bewertungen: 0
- Ø Bewertung:
- Medium: Buch
- Veröffentlicht: 12.07.2023
- Genre: Krimi
Data and Applications Security and Privacy XXXVII
The 19 full papers presented together with 5 short papers were carefully reviewed and selected from 56 submissions. The conference focuses on secure data sharing; access control and vulnerability assessment; machine learning; and mobile applications.
- Autor: Dolev, Shlomi
- Anzahl Bewertungen: 0
- Ø Bewertung:
- Medium: Buch
- Veröffentlicht: 13.07.2023
- Genre: Krimi
Cyber Security, Cryptology, and Machine Learning
The 21 full and 15 short papers were carefully reviewed and selected from 70 submissions. They deal with the theory, design, analysis, implementation, and application of cyber security, cryptography and machine learning systems and networks, and conceptually innovative topics in these research areas.
- Autor: Takada, Hideyuki
- Anzahl Bewertungen: 0
- Ø Bewertung:
- Medium: Buch
- Veröffentlicht: 23.08.2023
- Genre: Sonstiges
Collaboration Technologies and Social Computing
This book constitutes the refereed proceedings of the 29th International Conference on Collaboration Technologies and Social Computing, CollabTech 2023, held in Osaka, Japan, during August 29–September 1, 2023, in hybrid mode.
The 8 full papers presented in this book together with 12 short papers were carefully reviewed and selected from 31 submissions.The papers focus on innovative technical, human and organizational approaches to expand collaboration support including computer science, management science, design science, cognitive and social science.
- Autor: Bienz, Amanda
- Anzahl Bewertungen: 0
- Ø Bewertung:
- Medium: Buch
- Veröffentlicht: 25.08.2023
- Genre: Sonstiges
High Performance Computing
This volume constitutes the papers of several workshops which were held in conjunction with the 38th International Conference on High Performance Computing, ISC High Performance 2023, held in Hamburg, Germany, during May 21–25, 2023.
The 49 revised full papers presented in this book were carefully reviewed and selected from 70 submissions.
ISC High Performance 2023 presents the following workshops:
- 2nd International Workshop on Malleability Techniques Applications in High-Performance Computing (HPCMALL)
- 18th Workshop on Virtualization in High-Performance Cloud Computing (VHPC 23)
- HPC I/O in the Data Center (HPC IODC)
- Workshop on Converged Computing of Cloud, HPC, and Edge (WOCC’23)
- 7th International Workshop on In Situ Visualization (WOIV’23)
- Workshop on Monitoring and Operational Data Analytics (MODA23)
- 2nd Workshop on Communication, I/O, and Storage at Scale on Next-Generation Platforms: Scalable Infrastructures
- First International Workshop on RISC-V for HPC
- Second Combined Workshop on Interactive and Urgent Supercomputing (CWIUS)
- HPC on Heterogeneous Hardware (H3)
- Autor: Ronzhin, Andrey
- Anzahl Bewertungen: 0
- Ø Bewertung:
- Medium: Buch
- Veröffentlicht: 05.09.2023
- Genre: Roman
Interactive Collaborative Robotics
The 33 full papers included in this book were carefully reviewed and selected from 56 submissions. They were organized in topical sections as follows: focused the foundations and means of collaborative behavior of one or more robots physically interacting with hu-mans in operational environments configured with embedded sensor networks and cloud services under uncertainty and environmental variability.
- Autor: Shikata, Junji
- Anzahl Bewertungen: 0
- Ø Bewertung:
- Medium: Buch
- Veröffentlicht: 20.09.2023
- Genre: Krimi
Advances in Information and Computer Security
This book constitutes the refereed proceedings of the 18th International Workshop on Security, IWSEC 2023, which took place as a hybrid event in Yokohama, Japan, during August 29–31, 2023. This event was held in hybrid mode.
The 14 full papers presented in this book were carefully reviewed and selected from 47 submissions. They were organized in topical sections as follows: System and Hardware Security; Symmetric Key Cryptography; Public Key Cryptography; Zero Knowledge Proofs; and Card Based Cryptography.
- Autor: Zhou, Jianying
- Anzahl Bewertungen: 0
- Ø Bewertung:
- Medium: Buch
- Veröffentlicht: 22.09.2023
- Genre: Krimi
Applied Cryptography and Network Security Workshops
The 34 full papers and 13 poster papers presented in this volume were carefully reviewed and selected from 76 submissions. They stem from the following workshops:
- Autor: Fensel, Anna
- Anzahl Bewertungen: 0
- Ø Bewertung:
- Medium: Buch
- Veröffentlicht: 15.10.2023
- Genre: Roman
Rules and Reasoning
The 13 full papers and 3 short papers included in these proceedings were carefully reviewed and selected from 46 submissions. They focus on all aspects of theoretical advances; novel technologies; innovative applications; knowledge representation; reasoning with rules; and research, development, applications of rule-based systems.
- Autor: Quaresma, Paulo
- Anzahl Bewertungen: 0
- Ø Bewertung:
- Medium: Buch
- Veröffentlicht: 15.11.2023
- Genre: Sonstiges
Intelligent Data Engineering and Automated Learning – IDEAL 2023
The 45 full papers and 4 short papers presented in this book were carefully reviewed and selected from 77 submissions. IDEAL 2023 is focusing on big data challenges, machine learning, deep learning, data mining, information retrieval and management, bio-/neuro-informatics, bio-inspired models, agents and hybrid intelligent systems, and real-world applications of intelligence techniques and AI.
The papers are organized in the following topical sections: main track; special session on federated learning and (pre) aggregation in machine learning; special session on intelligent techniques for real-world applications of renewable energy and green transport; and special session on data selection in machine learning.
- Autor: Fritsch, Lothar
- Anzahl Bewertungen: 0
- Ø Bewertung:
- Medium: Buch
- Veröffentlicht: 13.12.2023
- Genre: Krimi
Secure IT Systems
This book constitutes the proceedings of the 28th Nordic Conference, NordSec 2023, held in Oslo, Norway, during November 16–17, 2023.
The 18 full papers included in this volume were carefully reviewed and selected from 55 submissions. This volume focuses on a broad range of topics within IT security and privacy.
- Autor: Janssen, Marijn
- Anzahl Bewertungen: 0
- Ø Bewertung:
- Medium: Buch
- Veröffentlicht: 15.12.2023
- Genre: Sonstiges
New Sustainable Horizons in Artificial Intelligence and Digital Solutions
The 29 full papers and 2 short papers presented in this volume were carefully reviewed and selected from 68 submissions. The contributions were organized in topical sections as follows: Artificial Intelligence and Algorithm; Digital Transformation and New Technologies; and Sustainable Technologies and Smart Cities.
- Autor: Ben Hedia, Belgacem
- Anzahl Bewertungen: 0
- Ø Bewertung:
- Medium: Buch
- Veröffentlicht: 19.12.2023
- Genre: Sonstiges
Verification and Evaluation of Computer and Communication Systems
- Autor: Fu, Jie
- Anzahl Bewertungen: 0
- Ø Bewertung:
- Medium: Buch
- Veröffentlicht: 29.12.2023
- Genre: Krimi
Decision and Game Theory for Security
The 19 full papers and 4 short papers included in this book were carefully reviewed and selected from 33 submissions. They were organized in topical sections as follows: Mechanism design and imperfect information, Security Games, Learning in security games, Cyber deception, Economics of security, Information and privacy and Short articles.
- Autor: Yung, Moti
- Anzahl Bewertungen: 0
- Ø Bewertung:
- Medium: Buch
- Veröffentlicht: 30.12.2023
- Genre: Krimi
Science of Cyber Security
This book constitutes the refereed proceedings of the 5th International Conference on Science of Cyber Security, SciSec 2023, held in Melbourne, VIC, Australia, during July 11–14, 2023.
- Autor: Tsudik, Gene
- Anzahl Bewertungen: 0
- Ø Bewertung:
- Medium: Buch
- Veröffentlicht: 11.01.2024
- Genre: Krimi
Computer Security – ESORICS 2023
The four-volume set LNCS 14344-14347 constitutes the refereed proceedings of the 28th European Symposium on Research in Computer Security, ESORICS 2023, which took place in The Hague, The Netherlands, during September 25-29, 2023.
The 93 full papers presented in these proceedings were carefully reviewed and selected from 478 submissions. They were organized in topical sections as follows:
Part I: Crypto.Part II: Network, web and internet; privacy; and remote.
Part III: Attacks; blockchain; and miscellaneous.
Part IV: Machine learning; software and systems security.- Autor: Manulis, Mark
- Anzahl Bewertungen: 0
- Ø Bewertung:
- Medium: Buch
- Veröffentlicht: 21.01.2024
- Genre: Krimi
Innovative Security Solutions for Information Technology and Communications
This book constitutes revised selected papers from the thoroughly refereed conference proceedings of the 16th International Conference on Innovative Security Solutions for Information Technology and Communications, SecITC 2023, held in Bucharest, Romania, in November 2023.
The 14 full papers included in the book were carefully reviewed and selected from 57 submissions. They focus on all theoretical and practical aspects related to information technology and communications security.
- Autor: Rudinac, Stevan
- Anzahl Bewertungen: 0
- Ø Bewertung:
- Medium: Buch
- Veröffentlicht: 28.01.2024
- Genre: Sonstiges
MultiMedia Modeling
This book constitutes the refereed proceedings of the 30th International Conference on MultiMedia Modeling, MMM 2024, held in Amsterdam, The Netherlands, during January 29–February 2, 2024.
The 112 full papers included in this volume were carefully reviewed and selected from 297 submissions. The MMM conference were organized in topics related to multimedia modelling, particularly: audio, image, video processing, coding and compression; multimodal analysis for retrieval applications, and multimedia fusion methods.- Autor: Rudinac, Stevan
- Anzahl Bewertungen: 0
- Ø Bewertung:
- Medium: Buch
- Veröffentlicht: 29.01.2024
- Genre: Sonstiges
MultiMedia Modeling
This book constitutes the refereed proceedings of the 30th International Conference on MultiMedia Modeling, MMM 2024, held in Amsterdam, The Netherlands, during January 29–February 2, 2024.
The 112 full papers included in this volume were carefully reviewed and selected from 297 submissions. The MMM conference were organized in topics related to multimedia modelling, particularly: audio, image, video processing, coding and compression; multimodal analysis for retrieval applications, and multimedia fusion methods.- Autor: De Marsico, Maria
- Anzahl Bewertungen: 0
- Ø Bewertung:
- Medium: Buch
- Veröffentlicht: 22.02.2024
- Genre: Sonstiges
Pattern Recognition Applications and Methods
This book constitutes the thoroughly refereed and revised selected papers from the 12th International Conference on Pattern Recognition Applications and Methods, ICPRAM 2023, held in Lisbon, Portugal, during February 22–24, 2023.
The 28 full papers and 42 short papers included in this book were carefully reviewed and selected from 157 submissions. They were organized in topical sections as follows: theory and methods and applications.
- Autor: Rudinac, Stevan
- Anzahl Bewertungen: 0
- Ø Bewertung:
- Medium: Buch
- Veröffentlicht: 15.04.2024
- Genre: Sonstiges
MultiMedia Modeling
This book constitutes the refereed proceedings of the 30th International Conference on MultiMedia Modeling, MMM 2024, held in Amsterdam, The Netherlands, during January 29–February 2, 2024.
The 120 full papers included in this volume were carefully reviewed and selected from 297 submissions. The MMM conference were organized in topics related to multimedia modelling, particularly: audio, image, video processing, coding and compression; multimodal analysis for retrieval applications, and multimedia fusion methods.- Autor: Mosbah, Mohamed
- Anzahl Bewertungen: 0
- Ø Bewertung:
- Medium: Buch
- Veröffentlicht: 25.04.2024
- Genre: Krimi
Foundations and Practice of Security
This book constitutes the refereed proceedings of the 16th International Symposium on Foundations and Practice of Security, FPS 2023, held in Bordeaux, France, during December 11–13, 2023.
The 27 regular and 8 short papers presented in this book were carefully reviewed and selected from 80 submissions. The papers have been organized in the following topical sections:Part I: AI and cybersecurity, security analysis, phishing and social network, vulnerabilities and exploits, network and system threat, malware analysis.
Part II : security design, short papers.
- Autor: Mosbah, Mohamed
- Anzahl Bewertungen: 0
- Ø Bewertung:
- Medium: Buch
- Veröffentlicht: 25.04.2024
- Genre: Krimi
Foundations and Practice of Security
This book constitutes the refereed proceedings of the 16th International Symposium on Foundations and Practice of Security, FPS 2023, held in Bordeaux, France, during December 11–13, 2023.
The 27 regular and 8 short papers presented in this book were carefully reviewed and selected from 80 submissions. The papers have been organized in the following topical sections:
Part I: AI and cybersecurity, security analysis, phishing and social network, vulnerabilities and exploits, network and system threat, malware analysis.
Part II : security design, short papers.
- Autor: Homma, Naofumi
- Anzahl Bewertungen: 0
- Ø Bewertung:
- Medium: Buch
- Veröffentlicht: 30.04.2024
- Genre: Krimi
Constructive Side-Channel Analysis and Secure Design
This book constitutes the refereed proceedings of the 15th International Workshop on Constructive Side-Channel Analysis and Secure Design, COSADE 2024, held in Gardanne, France, during April 9–10, 2024.
The 14 full papers included in this book were carefully reviewed and selected from 42 submissions. They were organized in topical sections as follows: Analyses and Tools; Attack Methods; Deep-Learning-Based Side-Channel Attacks; PUF/RNG; and Cryptographic Implementations.
- Autor: Mandviwalla, Munir
- Anzahl Bewertungen: 0
- Ø Bewertung:
- Medium: Buch
- Veröffentlicht: 22.05.2024
- Genre: Sonstiges
Design Science Research for a Resilient Future
This book constitutes the proceedings of the 19th International Conference on Design Science Research in Information Systems and Technology, DESRIST 2024, which was held in Trollhättan, Sweden, during June 3–5, 2024.
The 30 full papers presented in this book were carefully reviewed and selected from 69 submissions. The papers are divided into the following topical sections: DSR for a resilient world (theme track); general track; DSR methods and education; DSR in practice; and emerging topics in DSR.
- Autor: Benz, Nathaniel
- Anzahl Bewertungen: 0
- Ø Bewertung:
- Medium: Buch
- Veröffentlicht: 28.05.2024
- Genre: Sonstiges
NASA Formal Methods
This LNCS 14627 conference volume constitutes the proceedings of the 16th International Symposium on NASA Formal Methods, NFM 2024, held in Moffett Field, CA, USA in June 2024. The 20 full papers together with 6 short papers included in this volume were carefully reviewed and selected from 68 submissions.
The conference focuses on the on formal techniques for software and system assurance for applications in space, aviation, robotics, and other NASA-relevant safety-critical systems.
- Autor: Pickl, Stefan
- Anzahl Bewertungen: 0
- Ø Bewertung:
- Medium: Buch
- Veröffentlicht: 27.06.2024
- Genre: Krimi
Critical Information Infrastructures Security
This book constitutes the refereed proceedings of the 18th International Conference on Critical Information Infrastructures Security, CRITIS 2023, held in Helsinki region, Finland, during September 13–15 2023.
The 13 full papers and 3 short papers and one Paper in Progress were carefully selected from 25 submissions. The conference addressed four scientific focus areas, namely information, infrastructures, security and hybrid threats in an interdisciplinary manner and specifically in the context-based analyses and complex optimization methods.
- Autor: Maggi, Federico
- Anzahl Bewertungen: 0
- Ø Bewertung:
- Medium: Buch
- Veröffentlicht: 11.07.2024
- Genre: Krimi
Detection of Intrusions and Malware, and Vulnerability Assessment
This book constitutes the proceedings of the 21st International Conference on Detection of Intrusions and Malware, and Vulnerability Assessment, DIMVA 2024, held in Lausanne, Switzerland, during July 17–19, 2024.
The 22 full papers and 6 short paper presented in this volume were carefully reviewed and selected from 110 submissions. The papers are organized in thematical sections named: vulnerability detection and defense; malware and threats; mobile and web application security; AI for security; hardware and firmware security; cyber physical systems and IoT.
- Autor: Sudre, Carole H.
- Anzahl Bewertungen: 0
- Ø Bewertung:
- Medium: Buch
- Veröffentlicht: 02.10.2024
- Genre: Sonstiges
Uncertainty for Safe Utilization of Machine Learning in Medical Imaging
This book constitutes the refereed proceedings of the 6th Workshop on Uncertainty for Safe Utilization of Machine Learning in Medical Imaging, UNSURE 2024, held in conjunction with MICCAI 2024, Marrakesh, Morocco, on October 10, 2024.
The 20 full papers presented in this book were carefully reviewed and selected from 28 submissions. They are organized in the following topical sections: annotation uncertainty; clinical implementation of uncertainty modelling and risk management in clinical pipelines; out of distribution and domain shift identification and management; uncertainty modelling and estimation.
- Autor: Wu, Jia
- Anzahl Bewertungen: 0
- Ø Bewertung:
- Medium: Buch
- Veröffentlicht: 05.10.2024
- Genre: Sonstiges
Computational Mathematics Modeling in Cancer Analysis
This book constitutes the refereed proceedings of Third International Workshop on Computational Mathematics Modeling in Cancer Analysis, CMMCA 2024, held in Marrakesh, Morocco, on October 6, 2024, in conjunction with MICCAI 2024.
The 12 full papers presented in this book were carefully reviewed and selected from 14 submissions. CMMCA serves as a platform for collaboration among professionals in mathematics, engineering, computer science, and medicine, focusing on innovative mathematical methods for analyzing complex cancer data.
- Autor: Julian, Vicente
- Anzahl Bewertungen: 0
- Ø Bewertung:
- Medium: Buch
- Veröffentlicht: 20.11.2024
- Genre: Sonstiges
Intelligent Data Engineering and Automated Learning – IDEAL 2024
This two-volume set, LNCS 15346 and LNCS 15347, constitutes the proceedings of the 25th International Conference on Intelligent Data Engineering and Automated Learning, IDEAL 2024, held in Valencia, Spain, during November 20–22, 2024.
The 86 full papers and 6 short papers presented in this book were carefully reviewed and selected from 130 submissions. IDEAL 2024 is focusing on Big Data Analytics and Privacy, Machine Learning & Deep Learning for Real-World Applications, Data Mining and Pattern Recognition, Information Retrieval and Management, Bio and Neuro-Informatics, and Hybrid Intelligent Systems and Agents.
- Autor: Julian, Vicente
- Anzahl Bewertungen: 0
- Ø Bewertung:
- Medium: Buch
- Veröffentlicht: 20.11.2024
- Genre: Sonstiges
Intelligent Data Engineering and Automated Learning – IDEAL 2024
This two-volume set, LNCS 15346 and LNCS 15347, constitutes the proceedings of the 25th International Conference on Intelligent Data Engineering and Automated Learning, IDEAL 2024, held in Valencia, Spain, during November 20–22, 2024.
The 86 full papers and 6 short papers presented in this book were carefully reviewed and selected from 130 submissions. IDEAL 2024 is focusing on Big Data Analytics and Privacy, Machine Learning & Deep Learning for Real-World Applications, Data Mining and Pattern Recognition, Information Retrieval and Management, Bio and Neuro-Informatics, and Hybrid Intelligent Systems and Agents.
- Autor: Weiland, Michèle
- Anzahl Bewertungen: 0
- Ø Bewertung:
- Medium: Buch
- Veröffentlicht: 14.12.2024
- Genre: Sonstiges
High Performance Computing. ISC High Performance 2024 International Workshops
This book constitutes the refereed workshop proceedings from the 39th International conference on High Performance Computing, ISC High Performance 2024, held in Hamburg, Germany, in May 2024.
The 34 full papers presented here were carefully reviewed and selected from 50 submissions. These proceedings include papers from the following workshops:-
- Compiler-Assisted Correctness Checking and Performance Optimization for HPC Workshop (C3PO 2024)
- HPC on Heterogeneous Hardware Workshop (H3 2024)
- Third Workshop on Communication, I/O, and Storage at Scale on Next-Generation Platforms – Scalable Infrastructures (ISC 2024 IXPUG)
- HPC I/O in the Data Center Workshop (HPC-IODC 2024)
- Third Combined Workshop on Interactive and Urgent Supercomputing (CW-IUS 2024)
- 5th ISC HPC International Workshop on Monitoring & Operational Data Analytics (MODA24)
- Fourth International Workshop on RISC-V for HPC
- 2nd International Workshop on Sustainable Supercomputing
- Second International Workshop on Converged Computing on Edge, Cloud, and HPC (WOCC’24)
8th International Workshop on In Situ Visualization (WOIV’24)
Chapter “Interactive in Situ Visualization” is available open access under a Creative Commons Attribution 4.0 International License via link.springer.com.
- Autor: Menéndez, Héctor D.
- Anzahl Bewertungen: 0
- Ø Bewertung:
- Medium: Buch
- Veröffentlicht: 25.01.2025
- Genre: Sonstiges
Testing Software and Systems
This book constitutes the refereed proceedings of the 36th IFIP WG 6.1 International Conference on Testing Software and Systems, ICTSS 2024, held in London, UK, during October 30–November 1, 2024.
The 17 full papers and 5 short papers included in this book were carefully reviewed and selected from 40 submissions. They were organized in topical sections as follows: Best Paper Award; Industry and Challenge Tracks; Mutation Testing and Code Generation; Advancing Code Vulnerability Detection; Short Papers; Tutorial; Journal First; Health Track; Innovations in Software Testing and AI Compliance; Improving Software Testing Reliability and Advancements in Testing Methodologies.
- Autor: Horn Iwaya, Leonardo
- Anzahl Bewertungen: 0
- Ø Bewertung:
- Medium: Buch
- Veröffentlicht: 29.01.2025
- Genre: Krimi
Secure IT Systems
This book constitutes the refereed proceedings of the 29th International Conference on Secure IT Systems, NordSec 2024, held in Karlstad, Sweden, during November 6–7, 2024.
The 25 full papers presented in this book were carefully reviewed and selected from 59 submissions. They focus on topics such as: Authentication; Cryptography; Cyber-Physical Systems; Cybersecurity and Policy; LLMs for Security; Formal Verification; Mobile and IoT; Network Security; and Privacy.
- Autor: Meng, Weizhi
- Anzahl Bewertungen: 0
- Ø Bewertung:
- Medium: Buch
- Veröffentlicht: 13.03.2025
- Genre: Krimi
Attacks and Defenses for the Internet-of-Things
This book constitutes the referred proceedings of the 7th International Conference on Attacks and Defenses for Internet-of-Things, ADIoT 2024, held as an hybrid event, in Hangzhou, China, during December 13–14, 2024.
The 10 full papers were carefully reviewed and selected from 41 submissions.This conference focuses on both sides of IoT attacks and defenses, and seek original submissions that discuss either practical or theoretical solutions to identify IoT vulnerabilities and IoT security mechanisms.
- Autor: Garcia-Alfaro, Joaquin
- Anzahl Bewertungen: 0
- Ø Bewertung:
- Medium: Buch
- Veröffentlicht: 02.04.2025
- Genre: Sonstiges
Computer Security. ESORICS 2024 International Workshops
This two-volume set LNCS 15263 and LNCS 15264 constitutes the refereed proceedings of eleven International Workshops which were held in conjunction with the 29th European Symposium on Research in Computer Security, ESORICS 2024, held in Bydgoszcz, Poland, during September 16–20, 2024.
The papers included in these proceedings stem from the following workshops:
19th International Workshop on Data Privacy Management, DPM 2024, which accepted 7 full papers and 6 short papers out of 24 submissions;
8th International Workshop on Cryptocurrencies and Blockchain Technology, CBT 2024, which accepted 9 full papers out of 17 submissions;
10th Workshop on the Security of Industrial Control Systems and of Cyber-Physical Systems, CyberICPS 2024, which accepted 9 full papers out of 17 submissions;
International Workshop on Security and Artificial Intelligence, SECAI 2024, which accepted 10 full papers and 5 short papers out of 42 submissions;
Workshop on Computational Methods for Emerging Problems in Disinformation Analysis, DisA 2024, which accepted 4 full papers out of 8 submissions;
5th International Workshop on Cyber-Physical Security for Critical Infrastructures Protection, CPS4CIP 2024, which accepted 4 full papers out of 9 submissions;
3rd International Workshop on System Security Assurance, SecAssure 2024, which accepted 8 full papers out of 14 submissions.
- Autor: Chamberland, Maxime
- Anzahl Bewertungen: 0
- Ø Bewertung:
- Medium: Buch
- Veröffentlicht: 18.04.2025
- Genre: Sonstiges
Computational Diffusion MRI
This book constitutes the proceedings of the 15th International Workshop, CDMRI 2024, held in conjunction with MICCAI 2024, the 27th International Conference on Medical Image Computing and Computer-Assisted Intervention. The conference took place in Marrakesh, Morocco, October 6, 2024.
The 19 full papers presented in this book were carefully reviewed and selected from 22 submissions.
- Autor: Adi, Kamel
- Anzahl Bewertungen: 0
- Ø Bewertung:
- Medium: Buch
- Veröffentlicht: 01.05.2025
- Genre: Krimi
Foundations and Practice of Security
This two-volume set constitutes the refereed proceedings of the 17th International Symposium on Foundations and Practice of Security, FPS 2024, held in Montréal, QC, Canada, during December 09–11, 2024.
The 28 full and 11 short papers presented in this book were carefully reviewed and selected from 75 submissions. The papers were organized in the following topical sections:
Part I: Critical issues of protecting systems against digital threats,considering financial, technological, and operational implications; Automating and enhancing security mechanisms in software systems and data management; Cybersecurity and AI when applied to emerging technologies; Cybersecurity and Ethics; Cybersecurity and privacy in connected and autonomous systems for IoT, smart environments, and criticalinfrastructure; New trends in advanced cryptographic protocols. Part II: Preserving privacy and maintaining trust for end users in a complex and numeric cyberspace; Intersecting security, privacy, and machine learning techniques to detect, mitigate, and prevent threats; New trends of machine leaning and AI applied to cybersecurity.
- Autor: Jager, Tibor
- Anzahl Bewertungen: 0
- Ø Bewertung:
- Medium: Buch
- Veröffentlicht: 08.05.2025
- Genre: Sonstiges
Public-Key Cryptography – PKC 2025
The five-volume set LNCS 15674-15678 constitutes the refereed proceedings of the 28th IACR International Conference on Practice and Theory of Public Key Cryptography, PKC 2025, held in Røros, Norway, during May 12–15, 2025.
The 60 papers included in these proceedings were carefully reviewed and selected from 199 submissions. They are grouped into these topical sections: MPC and friends; advanced PKE; security of post-quantum signatures; proofs and arguments; multi-signatures; protocols; foundations of lattices and LPN; threshold signatures; isogenies and group actions; secure computation; security against real-world attacks; batch arguments and decentralized encryption; and cryptography for blockchains.
- Autor: Jager, Tibor
- Anzahl Bewertungen: 0
- Ø Bewertung:
- Medium: Buch
- Veröffentlicht: 08.05.2025
- Genre: Sonstiges
Public-Key Cryptography – PKC 2025
The five-volume set LNCS 15674-15678 constitutes the refereed proceedings of the 28th IACR International Conference on Practice and Theory of Public Key Cryptography, PKC 2025, held in Røros, Norway, during May 12–15, 2025.
The 60 papers included in these proceedings were carefully reviewed and selected from 199 submissions. They are grouped into these topical sections: MPC and friends; advanced PKE; security of post-quantum signatures; proofs and arguments; multi-signatures; protocols; foundations of lattices and LPN; threshold signatures; isogenies and group actions; secure computation; security against real-world attacks; batch arguments and decentralized encryption; and cryptography for blockchains.
- Autor: Jager, Tibor
- Anzahl Bewertungen: 0
- Ø Bewertung:
- Medium: Buch
- Veröffentlicht: 08.05.2025
- Genre: Sonstiges
Public-Key Cryptography – PKC 2025
The five-volume set LNCS 15674-15678 constitutes the refereed proceedings of the 28th IACR International Conference on Practice and Theory of Public Key Cryptography, PKC 2025, held in Røros, Norway, during May 12–15, 2025.
The 60 papers included in these proceedings were carefully reviewed and selected from 199 submissions. They are grouped into these topical sections: MPC and friends; advanced PKE; security of post-quantum signatures; proofs and arguments; multi-signatures; protocols; foundations of lattices and LPN; threshold signatures; isogenies and group actions; secure computation; security against real-world attacks; batch arguments and decentralized encryption; and cryptography for blockchains.
- Autor: Jager, Tibor
- Anzahl Bewertungen: 0
- Ø Bewertung:
- Medium: Buch
- Veröffentlicht: 08.05.2025
- Genre: Sonstiges
Public-Key Cryptography – PKC 2025
The five-volume set LNCS 15674-15678 constitutes the refereed proceedings of the 28th IACR International Conference on Practice and Theory of Public Key Cryptography, PKC 2025, held in Røros, Norway, during May 12–15, 2025.
The 60 papers included in these proceedings were carefully reviewed and selected from 199 submissions. They are grouped into these topical sections: MPC and friends; advanced PKE; security of post-quantum signatures; proofs and arguments; multi-signatures; protocols; foundations of lattices and LPN; threshold signatures; isogenies and group actions; secure computation; security against real-world attacks; batch arguments and decentralized encryption; and cryptography for blockchains.
- Autor: Jager, Tibor
- Anzahl Bewertungen: 0
- Ø Bewertung:
- Medium: Buch
- Veröffentlicht: 08.05.2025
- Genre: Sonstiges
Public-Key Cryptography – PKC 2025
The five-volume set LNCS 15674-15678 constitutes the refereed proceedings of the 28th IACR International Conference on Practice and Theory of Public Key Cryptography, PKC 2025, held in Røros, Norway, during May 12–15, 2025.
The 60 papers included in these proceedings were carefully reviewed and selected from 199 submissions. They are grouped into these topical sections: MPC and friends; advanced PKE; security of post-quantum signatures; proofs and arguments; multi-signatures; protocols; foundations of lattices and LPN; threshold signatures; isogenies and group actions; secure computation; security against real-world attacks; batch arguments and decentralized encryption; and cryptography for blockchains.
- Autor: Adi, Kamel
- Anzahl Bewertungen: 0
- Ø Bewertung:
- Medium: Buch
- Veröffentlicht: 29.05.2025
- Genre: Krimi
Foundations and Practice of Security
This two-volume set constitutes the refereed proceedings of the 17th International Symposium on Foundations and Practice of Security, FPS 2024, held in Montréal, QC, Canada, during December 09–11, 2024.
The 28 full and 11 short papers presented in this book were carefully reviewed and selected from 75 submissions. The papers were organized in the following topical sections:
Part I: Critical issues of protecting systems against digital threats,considering financial, technological, and operational implications; Automating and enhancing security mechanisms in software systems and data management; Cybersecurity and AI when applied to emerging technologies; Cybersecurity and Ethics; Cybersecurity and privacy in connected and autonomous systems for IoT, smart environments, and critical
infrastructure; New trends in advanced cryptographic protocols. Part II: Preserving privacy and maintaining trust for end users in a complex and numeric cyberspace; Intersecting security, privacy, and machine learning techniques to detect, mitigate, and prevent threats; New trends of machine leaning and AI applied to cybersecurity.
- Autor: Caino-Lores, Silvina
- Anzahl Bewertungen: 0
- Ø Bewertung:
- Medium: Buch
- Veröffentlicht: 10.06.2025
- Genre: Sonstiges
Euro-Par 2024: Parallel Processing Workshops
The two-volume set LNCS 15385 + 15386 constitutes the proceedings of the workshops and associated events that were held in conjunction with the 30th European Conference on Parallel and Distributed Processing, Euro-Par 2024, which took place in Madrid, Spain, during August 26–30, 2024.
Overall, the Euro-Par Workshops received a total of 84 submissions of which 60 were accepted for presentation. They stem from the following workshops:
– The 1st European Workshop on Quantum Computing for High-Performance Computing (EUROQHPC 2024)
– The 19th Workshop on Virtualization in High-Performance Cloud Computing (VHPC 2024)
– The 1st Workshop in High-Performance Computing in Physics (PHYSHPC 2024)
– The 4th Workshop on Asynchronous Many-Task Systems for Exascale (AMTE 2024)
– The 3rd EuroHPC Workshop on Dynamic Resources in HPC (DYNRESHPC 2024)
– The 22nd International Workshop on Algorithms, Models and Tools for Parallel Computing on Heterogeneous Platforms (HETEROPAR 2024)
– The 1st Workshop on Next Steps in IoT-Edge-Cloud Continuum Evolution: Research and Practice (IECCONT 2024)
– The 1st Workshop about High-Performance e-Science (HIPES 2024)
– The 2nd International Workshop on Scalable Compute Continuum (WSCC 2024)
In addition, the proceedings contain 14 poster and demo papers that have been accepted from 30 submissions, and 18 contributions in the PhD Symposium track that were accepted from 22 submissions.
- Autor: Caino-Lores, Silvina
- Anzahl Bewertungen: 0
- Ø Bewertung:
- Medium: Buch
- Veröffentlicht: 11.06.2025
- Genre: Sonstiges
Euro-Par 2024: Parallel Processing Workshops
The two-volume set LNCS 15385 + 15386 constitutes the proceedings of the workshops and associated events that were held in conjunction with the 30th European Conference on Parallel and Distributed Processing, Euro-Par 2024, which took place in Madrid, Spain, during August 26–30, 2024.
Overall, the Euro-Par Workshops received a total of 84 submissions of which 60 were accepted for presentation. They stem from the following workshops:
– The 1st European Workshop on Quantum Computing for High-Performance Computing (EUROQHPC 2024)
– The 19th Workshop on Virtualization in High-Performance Cloud Computing (VHPC 2024)
– The 1st Workshop in High-Performance Computing in Physics (PHYSHPC 2024)
– The 4th Workshop on Asynchronous Many-Task Systems for Exascale (AMTE 2024)
– The 3rd EuroHPC Workshop on Dynamic Resources in HPC (DYNRESHPC 2024)
– The 22nd International Workshop on Algorithms, Models and Tools for Parallel Computing on Heterogeneous Platforms (HETEROPAR 2024)
– The 1st Workshop on Next Steps in IoT-Edge-Cloud Continuum Evolution: Research and Practice (IECCONT 2024)
– The 1st Workshop about High-Performance e-Science (HIPES 2024)
– The 2nd International Workshop on Scalable Compute Continuum (WSCC 2024)
In addition, the proceedings contain 14 poster and demo papers that have been accepted from 30 submissions, and 18 contributions in the PhD Symposium track that were accepted from 22 submissions.
- Autor: Egele, Manuel
- Anzahl Bewertungen: 0
- Ø Bewertung:
- Medium: Buch
- Veröffentlicht: 10.07.2025
- Genre: Krimi
Detection of Intrusions and Malware, and Vulnerability Assessment
The two-volume set LNCS 15747 and 15748 constitutes the refereed conference proceedings of the 12nd International Conference on Detection of Intrusions and Malware, and Vulnerability Assessment, DIMVA 2025, held in Graz, Austria, during July 9–11, 2025.
The 25 revised full papers and 11 posters are presented in these proceedings were carefully reviewed and selected from 103 submissions. The papers are organized in the following topical sections:
Part I: Web Security; Vulnerability Detection; Side channels; and Obfuscation.
Part II: AI/ML & Security; Android & Patches; OS & Network; and Resilient Systems.
- Autor: Egele, Manuel
- Anzahl Bewertungen: 0
- Ø Bewertung:
- Medium: Buch
- Veröffentlicht: 23.07.2025
- Genre: Krimi
Detection of Intrusions and Malware, and Vulnerability Assessment
The two-volume set LNCS 15747 and 15748 constitutes the refereed conference proceedings of the 12nd International Conference on Detection of Intrusions and Malware, and Vulnerability Assessment, DIMVA 2025, held in Graz, Austria, during July 9–11, 2025.
The 25 revised full papers and 11 posters are presented in these proceedings were carefully reviewed and selected from 103 submissions. The papers are organized in the following topical sections:
Part I: Web Security; Vulnerability Detection; Side channels; and Obfuscation.
Part II: AI/ML & Security; Android & Patches; OS & Network; and Resilient Systems.
- Autor: Morogan, Luciana
- Anzahl Bewertungen: 0
- Ø Bewertung:
- Medium: Buch
- Veröffentlicht: 27.07.2025
- Genre: Krimi
Innovative Security Solutions for Information Technology and Communications
This book constitutes revised selected papers from the thoroughly refereed conference proceedings of the 17th International Conference on Innovative Security Solutions for Information Technology and Communications, SecITC 2024, which took place in Bucharest, Romania, in November 2024.
The 16 full papers presented in these proceedings were carefully reviewed and selected from 49 submissions. The book also contains two invited talks. This conference is focusing on all theoretical and practical aspects related to information technology and communications security.
- Autor: Mata-Rivera, Miguel Félix
- Anzahl Bewertungen: 0
- Ø Bewertung:
- Medium: Buch
- Veröffentlicht: 17.08.2025
- Genre: Krimi
Web and Wireless Geographical Information Systems
This LNCS conference volume constitutes the proceedings of the 22nd International Symposium on Web and Wireless Geographical Information Systems, W2GIS 2025, in Mexico City, Mexico, held during September 8–9, 2025.
The 11 full papers presented in this volume were carefully reviewed and selected from 22 submissions.
They are grouped into the following topics: Advances in Geospatial Artificial Intelligence: From Pixel-level Vision to Large-Language Models; Data-driven Urban Health & Safety: Environmental Exposure, Crime, and Disease Dynamics; Location Intelligence for Urban Resources, Mobility, and Commerce.
- Autor: Curry, Edward
- Anzahl Bewertungen: 0
- Ø Bewertung:
- Medium: Buch
- Veröffentlicht: 29.09.2025
- Genre: Sonstiges
The Semantic Web: ESWC 2025 Satellite Events
This book constitutes the proceedings of the satellite events held at the XXX Semantic Web Conference, ESWC 2025, held in Portoroz, Slovenia, during June 1–2, 2025.
The 31 Posters & Demos papers are presented together with 12 PhD Symposium papers and 7 Industry papers in this book were carefully reviewed and selected from 43 Posters& Demo papers, 15 PHD Symsposium papers and 14 Industry papers.
The theme of the conference was “Empowering Knowledge through Semantics: From Knowledge Graphs to Neurosemantics”. The satellite events are an important aspect of facilitating the main conference discussion as well as fundamental questions about how we acquire, represent, use, and interact with knowledge and semantics.
The satellite events of ESWC 2025 include the poster and demo session, the PhD symposium, the industry track, project networking, and workshops and tutorials.
- Autor: Avni, Guy
- Anzahl Bewertungen: 0
- Ø Bewertung:
- Medium: Buch
- Veröffentlicht: 03.10.2025
- Genre: Sonstiges
AI Verification
This LNCS volume constitutes the proceedings of the Second International Symposium, SAIV 2025, in Zagreb, Croatia, during July 2025.
The scope of the topics was broadly categorized into two groups. The first group, formal methods for artificial intelligence, comprised: formal specifications for systems with AI components; formal methods for analyzing systems with AI components; formal synthesis methods of AI components; testing approaches for systems with AI components; statistical approaches for analyzing systems with AI components; and approaches for enhancing the explainability of systems with AI components. The second group, artificial intelligence for formal methods, comprised: AI methods for formal verification; AI methods for formal
synthesis; AI methods for safe control; and AI methods for falsification.
- Autor: Neuwirth, Sarah
- Anzahl Bewertungen: 0
- Ø Bewertung:
- Medium: Buch
- Veröffentlicht: 22.11.2025
- Genre: Sonstiges
- Autor: Steffen, Barbara
- Anzahl Bewertungen: 0
- Ø Bewertung:
- Medium: Buch
- Veröffentlicht: 29.11.2025
- Genre: Sonstiges
Let’s Talk AI
This unique open access volume represents an interdisciplinary dialog with top-class researchers and practitioners on the Artificial Intelligence revolution. The contributions derive from structured interviews with community leaders who examine recent developments in AI and offer predictions about its impact on science, technology, business, and society. The interviewees, leading thinkers and practitioners from fields such as Computer Science, Software Engineering, Philosophy, Psychology, and Law, gathered at the multidisciplinary event AISoLA, where they discussed developments in AI technologies, tools, and research, and these exchanges were shaped into this coherent survey.
In the debates surrounding the rapid advancement of AI it’s clear that while there is much sharing of ideas, in fact true cooperation and alignment is rare, most fields still operate in silos. Given the pervasive nature of AI, it’s critical that we move forward carefully to ensure that our decisions and progress are well-considered. This book serves as a call to action, reminding us of our collective responsibility to shape the future. The authors offer points of agreement and contrast, the reader will better understand how we may still maintain control over technological progress in AI and its societal impact.
- Autor: Akavia, Adi
- Anzahl Bewertungen: 0
- Ø Bewertung:
- Medium: Buch
- Veröffentlicht: 15.12.2025
- Genre: Sonstiges
Cyber Security, Cryptology, and Machine Learning
This volume constitutes the proceedings of 9th International Symposium on Cyber Security, Cryptology, and Machine Learning, CSCML 2025, in Be'er Sheva, Israel, during December 4–5, 2025.
The 17 regular papers and 9 short papers presented here were carefully reviewed and selected from 43 submissions. These papers focus on Cyber security design; secure software development methodologies; formal methods, semantics, and verification of secure systems; fault tolerance, reliability, and availability of distributed secure systems; game-theoretic approaches to secure computing; automatic recovery,
self-stabilizing, and self-organizing systems; communication, authentication, and identification security; cyber security for mobile systems and the Internet of Things; and much more.
- Autor: Taft, S. Tucker
- Anzahl Bewertungen: 0
- Ø Bewertung:
- Medium: Digital
- Veröffentlicht: 04.06.2027
- Genre: Sonstiges
Consolidated Ada 2022 Reference Manual. Volume 1 - Core Language
The Ada 2022 Reference Manual is an enhanced version of the text of International Standard ISO/IEC 8652/2023(E) for the programming language Ada. The Ada 2022 Reference Manual combines all of the previous corrections with changes and additions that improve the capabilities of the language and the reliability of programs written in the language. The Ada 2022 Reference Manual will replace the former versions as an indispensable working companion for anybody using Ada professionally or learning and studying the language systematically.
- Band: 13049
- Autor: Batina, Lejla
- Anzahl Bewertungen: 0
- Ø Bewertung:
- Medium: Buch
- Veröffentlicht: 08.04.2022
- Genre: Krimi
Security and Artificial Intelligence
The editors of this State-of-the-Art Survey invited a cross-disciplinary team of researchers to a Lorentz workshop in 2019 to improve collaboration in these areas. Some contributions were initiated at the event, others were developed since through further invitations, editing, and cross-reviewing. This contributed book contains 14 invited chapters that address side-channel attacks and fault injection, cryptographic primitives, adversarial machine learning, and intrusion detection. The chapters were evaluated based on their significance, technical quality, and relevance to the topics of security and AI, and each submission was reviewed in single-blindmode and revised.
- Band: 13175
- Autor: Renault, Éric
- Anzahl Bewertungen: 0
- Ø Bewertung:
- Medium: Buch
- Veröffentlicht: 23.03.2022
- Genre: Krimi
Machine Learning for Networking
- Band: 13195
- Autor: Ryan, Peter Y.A.
- Anzahl Bewertungen: 0
- Ø Bewertung:
- Medium: Buch
- Veröffentlicht: 13.10.2022
- Genre: Krimi
Innovative Security Solutions for Information Technology and Communications
The 22 full papers included in this book were carefully reviewed and selected from 40 submissions. They deal with emergent topics in security and privacy from different communities.
- Band: 13218
- Autor: Park, Jong Hwan
- Anzahl Bewertungen: 0
- Ø Bewertung:
- Medium: Buch
- Veröffentlicht: 24.07.2022
- Genre: Krimi
Information Security and Cryptology – ICISC 2021
This book constitutes selected papers from the 24th International Conference on Information Security and Cryptology, ICISC 2021, held in Seoul, South Korea, in December 2021.
The total of 23 papers presented in this volume were carefully reviewed and selected from 63 submissions. The papers are arranged by topic: Cryptographic Protocol in Quantum Computer Age; Security Analysis of Hash Algorithm; Security analysis of Symmetric Key Encryption Algorithm; Fault and Side-Channel Attack; Constructions and Designs; Quantum Circuit; Efficient Implementation. The aim of this conference was to provide an international forum for the latest results of research, development, and applications within the field of information security and cryptology.
- Band: 13285
- Autor: Zhou, Jianying
- Anzahl Bewertungen: 0
- Ø Bewertung:
- Medium: Buch
- Veröffentlicht: 25.09.2022
- Genre: Krimi
Applied Cryptography and Network Security Workshops
This book constitutes the proceedings of the satellite workshops held around the 20th International Conference on Applied Cryptography and Network Security, ACNS 2022, held in Rome, Italy, in June 2022. Due to the Corona pandemic the workshop was held as a virtual event.
The 31 papers presented in this volume were carefully reviewed and selected from 52 submissions. They stem from the following workshops:
– AIBlock: 4th ACNS Workshop on Application Intelligence and Blockchain Security– AIHWS: 3rd ACNS Workshop on Artificial Intelligence in Hardware Security
– AIoTS: 4th ACNS Workshop on Artificial Intelligence and Industrial IoT Security
– CIMSS: 2nd ACNS Workshop on Critical Infrastructure and Manufacturing System Security
– Cloud S&P: 4th ACNS Workshop on Cloud Security and Privacy
– SCI: 3rd ACNS Workshop on Secure Cryptographic Implementation– SecMT: 3rd ACNS Workshop on Security in Mobile Technologies
– SiMLA: 4th ACNS Workshop on Security in Machine Learning and its Applications
- Band: 13291
- Autor: Aïmeur, Esma
- Anzahl Bewertungen: 0
- Ø Bewertung:
- Medium: Buch
- Veröffentlicht: 16.06.2022
- Genre: Krimi
Foundations and Practice of Security
This book constitutes the revised selected papers of the 14th International Symposium on Foundations and Practice of Security, FPS 2021, held in Paris, France, in December 2021.
The 18 full papers and 9 short paper presented in this book were carefully reviewed and selected from 62 submissions. They cover a range of topics such as Analysis and Detection; Prevention and Efficiency; and Privacy by Design.
Chapters “A Quantile-based Watermarking Approach for Distortion Minimization”, “Choosing Wordlists for Password Guessing: An Adaptive Multi-Armed Bandit Approach” and “A Comparative Analysis of Machine Learning Techniques for IoT Intrusion Detection” are available open access under a Creative Commons Attribution 4.0 International License via link.springer.com.
- Band: 13300
- Autor: Kołodziej, Joanna
- Anzahl Bewertungen: 7
- Ø Bewertung: 3.8
- Medium: Buch
- Veröffentlicht: 07.04.2022
- Genre: Krimi
Cybersecurity of Digital Service Chains
This open access book presents the main scientific results from the H2020 GUARD project. The GUARD project aims at filling the current technological gap between software management paradigms and cybersecurity models, the latter still lacking orchestration and agility to effectively address the dynamicity of the former. This book provides a comprehensive review of the main concepts, architectures, algorithms, and non-technical aspects developed during three years of investigation; the description of the Smart Mobility use case developed at the end of the project gives a practical example of how the GUARD platform and related technologies can be deployed in practical scenarios.
We expect the book to be interesting for the broad group of researchers, engineers, and professionals daily experiencing the inadequacy of outdated cybersecurity models for modern computing environments and cyber-physical systems.- Band: 13301
- Autor: Dolev, Shlomi
- Anzahl Bewertungen: 0
- Ø Bewertung:
- Medium: Buch
- Veröffentlicht: 31.05.2022
- Genre: Krimi
Cyber Security, Cryptology, and Machine Learning
This book constitutes the refereed proceedings of the 6th International Symposium on Cyber Security Cryptography and Machine Learning, CSCML 2022, held in Be'er Sheva, Israel, in June - July 2022.
The 24 full and 11 short papers presented together with a keynote paper in this volume were carefully reviewed and selected from 53 submissions. They deal with the theory, design, analysis, implementation, or application of cyber security, cryptography and machine learning systems and networks, and conceptually innovative topics in these research areas.
- Band: 13358
- Autor: Cavallaro, Lorenzo
- Anzahl Bewertungen: 0
- Ø Bewertung:
- Medium: Buch
- Veröffentlicht: 25.06.2022
- Genre: Krimi
Detection of Intrusions and Malware, and Vulnerability Assessment
The 10 full papers and 1 short paper presented in this volume were carefully reviewed and selected from 39 submissions.
- Band: 13383
- Autor: Sural, Shamik
- Anzahl Bewertungen: 0
- Ø Bewertung:
- Medium: Buch
- Veröffentlicht: 13.07.2022
- Genre: Krimi
Data and Applications Security and Privacy XXXVI
The 12 full papers and 6 short papers presented were carefully reviewed and selected from 33 submissions. The conference covers research in data and applications security and privacy.
- Band: 13407
- Autor: Alcaraz, Cristina
- Anzahl Bewertungen: 0
- Ø Bewertung:
- Medium: Buch
- Veröffentlicht: 24.08.2022
- Genre: Krimi
Information and Communications Security
The 34 revised full papers presented in the book were carefully selected from 150 submissions
The papers are organized around the following topics: Cryptography, Authentication, Privacy and Anonymity, Attacks and Vulnerability Analysis, Artificial Intelligence for Detection, and Network Security and Forensics.
- Band: 13429
- Autor: Kő, Andrea
- Anzahl Bewertungen: 0
- Ø Bewertung:
- Medium: Buch
- Veröffentlicht: 29.07.2022
- Genre: Politik
Electronic Government and the Information Systems Perspective
- Band: 13504
- Autor: Cheng, Chen-Mou
- Anzahl Bewertungen: 0
- Ø Bewertung:
- Medium: Buch
- Veröffentlicht: 12.08.2022
- Genre: Krimi
Advances in Information and Computer Security
- Band: 13547
- Autor: Chen, Xiaofeng
- Anzahl Bewertungen: 0
- Ø Bewertung:
- Medium: Buch
- Veröffentlicht: 29.09.2022
- Genre: Krimi
Cyberspace Safety and Security
- Band: 13553
- Autor: Krimmer, Robert
- Anzahl Bewertungen: 2
- Ø Bewertung: 5.0
- Medium: Buch
- Veröffentlicht: 03.09.2022
- Genre: Krimi
Electronic Voting
This open access book LNCS 13353 constitutes the proceedings of the 7th International Conference on Electronic Voting, E-Vote-ID 2022, held in Bregenz, Austria, in October 2022. The 10 full papers presented were carefully reviewed and selected from 39 submissions.
The conference collected the most relevant debates on the development of Electronic Voting, from aspects relating to security and usability through to practical experiences and applications of voting systems, also including legal, social, or political aspects, amongst others.
- Band: 13554
- Autor: Atluri, Vijayalakshmi
- Anzahl Bewertungen: 0
- Ø Bewertung:
- Medium: Buch
- Veröffentlicht: 25.09.2022
- Genre: Krimi
Computer Security – ESORICS 2022
The 104 full papers and 6 poster papers presented in these proceedings were carefully reviewed and selected from 562 submissions. They were organized in topical sections as follows:
Part I: Blockchain security; privacy; crypto; attacks; sidechannels;Part II: Anonymity; cloud security; access control; authentication; digital signatures; IoT security; applications;
Part III: Formal analysis; Web security; hardware security; multiparty computation; ML techniques; cyber-physical systems security; network and software security; posters.- Band: 13556
- Autor: Atluri, Vijayalakshmi
- Anzahl Bewertungen: 0
- Ø Bewertung:
- Medium: Buch
- Veröffentlicht: 24.09.2022
- Genre: Krimi
Computer Security – ESORICS 2022
The 104 full papers and 6 poster papers presented in these proceedings were carefully reviewed and selected from 562 submissions. They were organized in topical sections as follows:
Part I: Blockchain security; privacy; crypto; attacks; sidechannels;Part II: Anonymity; cloud security; access control; authentication; digital signatures; IoT security; applications;
Part III: Formal analysis; Web security; hardware security; multiparty computation; ML techniques; cyber-physical systems security; network and software security; posters.- Band: 13580
- Autor: Su, Chunhua
- Anzahl Bewertungen: 0
- Ø Bewertung:
- Medium: Buch
- Veröffentlicht: 30.09.2022
- Genre: Krimi
Science of Cyber Security
The 36 full papers presented in this volume were carefully reviewed and selected from 88 submissions. The papers are organized in the following topical sections: blockchain and applications; cryptography and applications; network security; cyber-physical system; malware; mobile system security; system and web security; security in financial industry; social engineering and personalized security; privacy and anonymity.
- Band: 13620
- Autor: Su, Chunhua
- Anzahl Bewertungen: 0
- Ø Bewertung:
- Medium: Buch
- Veröffentlicht: 19.11.2022
- Genre: Krimi
Information Security Practice and Experience
This book constitutes the refereed proceedings of the 17th International Conference on Information Security Practice and Experience, ISPEC 2022, held in Taipei, Taiwan, in November 2022.
The 33 full papers together with 2 invited papers included in this volume were carefully reviewed and selected from 87 submissions.
The main goal of the conference is to promote research on new information security technologies, including their applications and their integration with IT systems in various vertical sectors.
- Band: 13719
- Autor: Ronzhin, Andrey
- Anzahl Bewertungen: 0
- Ø Bewertung:
- Medium: Buch
- Veröffentlicht: 18.12.2022
- Genre: Roman
Interactive Collaborative Robotics
This book constitutes the proceedings of the 7th International Conference on Interactive Collaborative Robotics, ICR 2022, held in Fuzhou, China, in December 2022.
The 25 papers presented were carefully reviewed and selected from 45 submissions. Challenges of human-robot interaction, robot control and behavior in social robotics and collaborative robotics, as well as applied robotic and cyber-physical systems are mainly discussed in the papers.
- Band: 13745
- Autor: Li, Wenjuan
- Anzahl Bewertungen: 0
- Ø Bewertung:
- Medium: Buch
- Veröffentlicht: 11.12.2022
- Genre: Krimi
Attacks and Defenses for the Internet-of-Things
The 7 full papers and 3 short papers were carefully reviewed and selected from 18 submissions.
This workshop focuses on IoT attacks and defenses and discusses either practical or theoretical solutions to identify IoT vulnerabilities and IoT security mechanisms.- Band: 13825
- Autor: Zhao, Xianfeng
- Anzahl Bewertungen: 0
- Ø Bewertung:
- Medium: Buch
- Veröffentlicht: 17.02.2023
- Genre: Krimi
Digital Forensics and Watermarking
The 14 full papers included in this book were carefully reviewed and selected from 30 submissions. They were organized in topical sections as follows: Steganology, Forensics and Security Analysis, Watermarking.